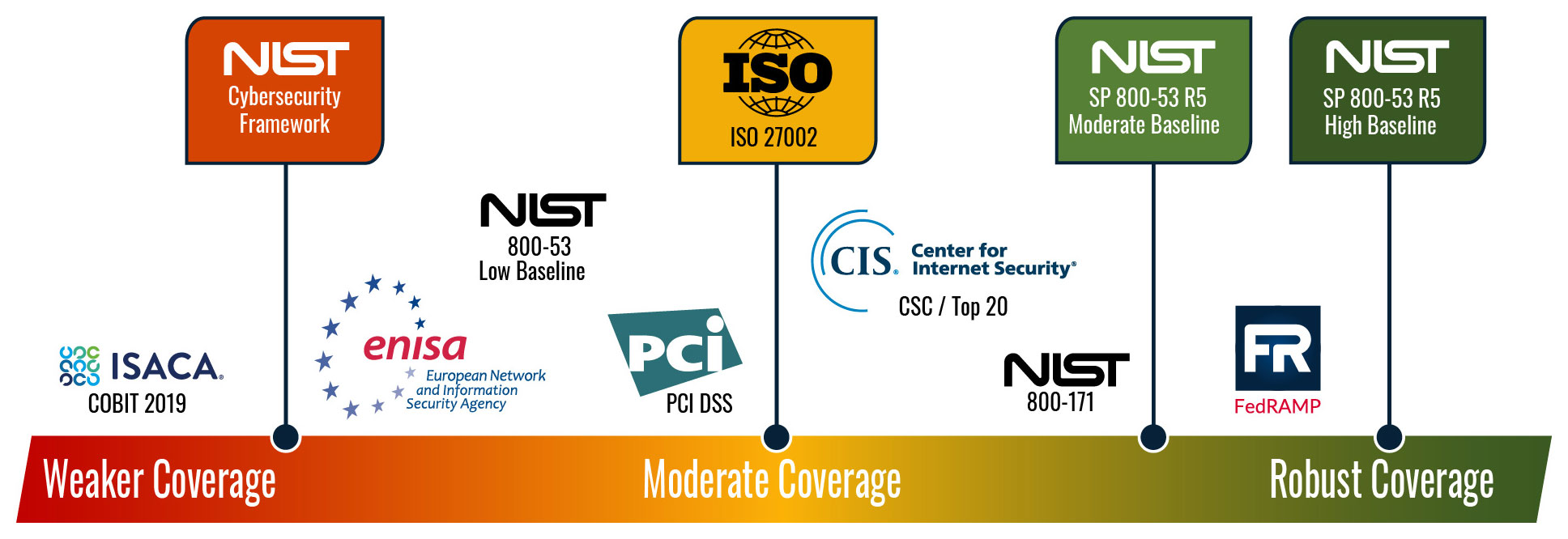
At Dewpoint, we believe in “Making IT Personal.” What does that mean for you? We know treading through the various cybersecurity standards can be daunting. So we simplified the process. If your organization needs to meet regulatory requirements or has a government or industry mandate, then The National Institute of Standards and Technology (NIST) standards are typically required. For example, companies that are part of the Defense Industrial Base (DIB) are being advised that they will require an assessment based on the NIST SP 800-171 framework to obtain a CMMC maturity rating. The NIST standards are applicable to any size organization.
- Cyber AB Registered Practitioner Organization
- Cyber AB Registered Practitioners
- Proven, repeatable process
- Actionable recommendations