

June 7, 2023
Cybersecurity plays a critical role in today’s industry. Protecting sensitive information is foundational to success. The Cybersecurity Maturity Model Certification (CMMC) is a framework designed to enhance the cybersecurity posture of companies working with the Department of Defense (DoD). Per the Department of Defense, “The program provides the Department increased assurance that contractors and subcontractors are meeting the cybersecurity requirements that apply to acquisition programs and systems that process controlled unclassified information.”
The CMMC 2.0 framework is structured into three levels, each representing a different degree of cybersecurity maturity. To achieve these levels, organizations must implement controls and practices appropriate to their operations. Key points to consider are:
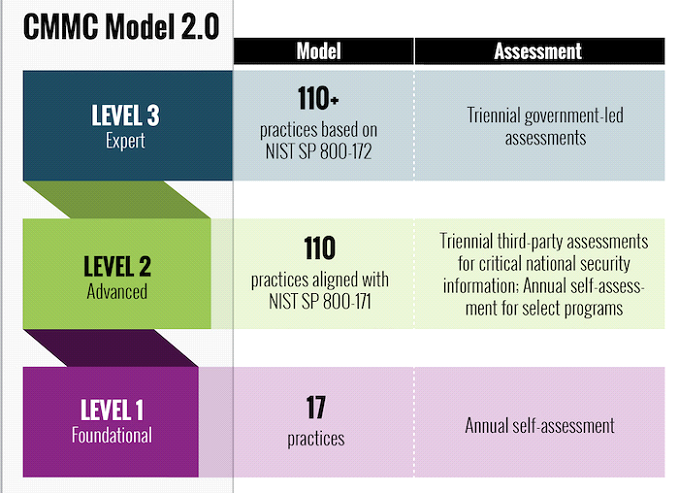
Level 1 – Foundational: Level 1 focuses on safeguarding Federal Contract Information (FCI). This level requires implementing basic cybersecurity practices, such as antivirus software and access controls. Organizations at this level must conduct annual security assessments with documented results. Organizations at this level may self-assess.
Level 2 – Advanced: Level 2 introduces additional controls for protecting Controlled Unclassified Information (CUI). Level 2 requires a more mature cybersecurity foundation. Organizations at this level must establish and document practices and policies to guide their cybersecurity efforts. They should implement and manage processes to detect and respond to common cyber threats effectively. If the organization’s CUI is critical to national security, the organization must complete, document, and submit a third-party party assessment every three years. If the CUI is not vital to national security, the organization may perform an annual self-assessment or hire a third party to complete the assessment.
Level 3 – Expert: Level 3 represents a higher level of cybersecurity maturity and builds upon the foundation established in Level 2. Organizations at this level must have a comprehensive and proactive approach to protect CUI. They must implement and manage a robust set of security controls and processes. Level 3 emphasizes implementing good cyber hygiene practices throughout the organization, including regularly reviewing and improving security measures. Compliance at this level is a matter of national security and requires a third-party assessment every three years with close government oversight.
CMMC provides a comprehensive approach to cybersecurity, ensuring that organizations have the necessary measures to protect sensitive information. Implementing CMMC controls can significantly reduce the risk of cyber threats, including data breaches, intellectual property theft, and unauthorized access.
Being CMMC compliant can give your organization a competitive edge when bidding for DoD contracts. As the DoD shifts towards making CMMC a requirement for contractors, having a higher CMMC level can set your organization apart from competitors, demonstrating your commitment to cybersecurity and protecting sensitive information.
Many DoD contracts and opportunities will require contractors to meet specific CMMC levels. By achieving these levels, your organization becomes eligible for a wider range of contracts, opening new avenues for growth and revenue.
CMMC compliance signifies a commitment to cybersecurity and safeguarding sensitive information. This commitment helps build trust with customers, partners, and stakeholders concerned about their data’s security. Meeting CMMC requirements can enhance your reputation and attract potential clients who prioritize cybersecurity.
To address CMMC gaps effectively, organizations should focus on implementing the following controls and practices:
Develop a robust risk management program that includes identifying and assessing risks, implementing appropriate controls, and continuously monitoring and improving security measures. This program should align with the CMMC requirements and address the specific risks associated with your organization’s operations.
Implement strong access controls to ensure only authorized personnel can access sensitive information. Examples include multi-factor authentication, role-based access controls, and regular access reviews.
Establish an effective incident response plan to promptly detect, respond to, and recover from security incidents. This plan should include procedures for reporting incidents, investigating their root causes, and implementing measures to prevent similar incidents in the future.
Conduct regular cybersecurity training sessions to educate employees about potential risks, safe browsing habits, and the importance of following security protocols. Promote a culture of cybersecurity awareness throughout the organization.
Would you like to know more about becoming CMMC compliant or moving to the next level? Dewpoint’s security experts will help you identify your security goals and build a path toward achieving them. Schedule a time to chat with one of our cybersecurity experts today.